Consider yourself as a network security specialist. As you try to secure the security posture of your environment
As you try to secure the security posture of your environment, you realize that different threats can interfere with the confidentiality
Consider yourself as a network security specialist. As you try to secure the security posture of your environment, you realize that different threats can interfere with the confidentiality, integrity, and availability of data-at-rest, data-in-transit, and processing. Some threats may affect only 1 of these elements of security (such as confidentiality only), and other threats affect more than one or even all these elements.
In this assignment, you will be evaluated on your asset protection skill.
Create a 1- to 2-page table in Microsoft®️ Word identifying a minimum of 6 threats, using the column headers and details below:
Column Headers
Threat
Threat to Type of Data
Confidentiality/Integrity/Availability
Mitigation Suggestion
Details Within Your Table
Identify relevant threats. List 1 per column.
Determine the type of data threatened (data-at-rest, data-in-transit, or processing) in the column.
Determine if confidentiality, integrity, or availability was affected. Use the labels C, I, and/or A in the column.
Describe the mitigation plan in 2 to 3 sentences in the column.
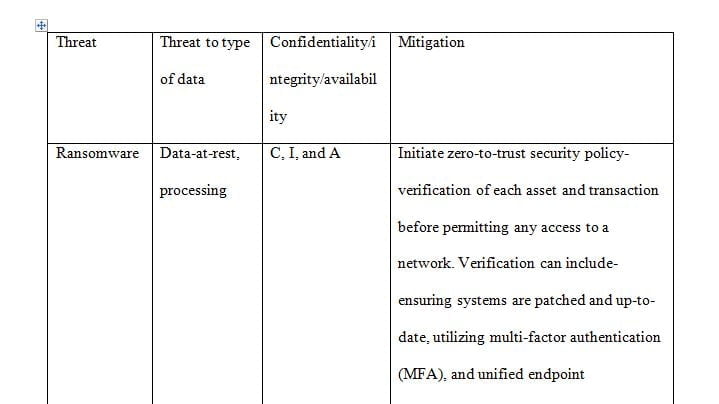
Example Table
Example Table
Include a short paragraph that highlights 2 access control techniques or policies that enforce security.
Cite at least 2 resources to support your assignment.
Format your assignment according to APA guidelines.
Submit your assignment.
Resources
Center for Writing Excellence
Reference and Citation Generator
Grammar Assistance
Answer preview for the paper on Consider yourself as a network security specialist. As you try to secure the security posture of your environment’
APA 715 words
Click the purchase button below to download full answer…….
